
We do applied Artificial Intelligence
Our mission
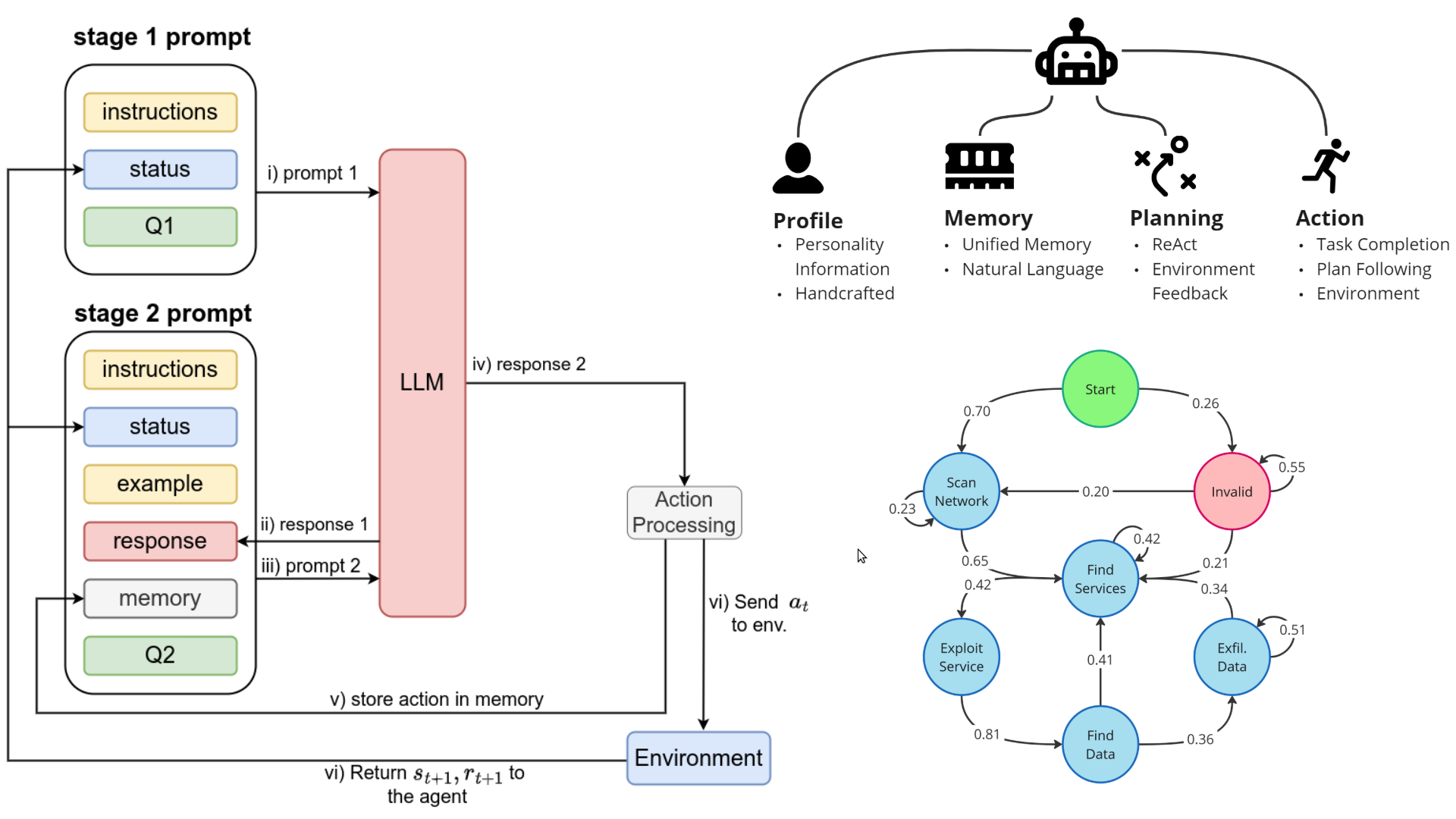
This research line explores the application of autonomous intelligent agents in cybersecurity, with a focus on both defensive and offensive operations. While defensive systems have received considerable attention, offensive agents play a crucial role in testing system resilience and improving defenses through realistic adversarial interaction. The project investigates how language models can be adapted for autonomous penetration testing, particularly examining the potential of smaller models for local deployment in environments with limited resources or strict confidentiality requirements. Through domain-specific fine-tuning techniques such as supervised fine-tuning and direct preference optimization, these models can be enhanced to operate effectively within cognitive architectures for autonomous decision-making. The research addresses the development of agents capable of exhibiting structured strategic behavior aligned with realistic attack stages including reconnaissance, privilege escalation, lateral movement, and data exfiltration. Evaluation is conducted in simulated network security environments designed for ethical cybersecurity research and aligned with real-world attack tactics. This work aims to advance the understanding of how locally deployed language models can support effective and transparent offensive operations in cybersecurity, contributing to improved defense mechanisms and system resilience testing.
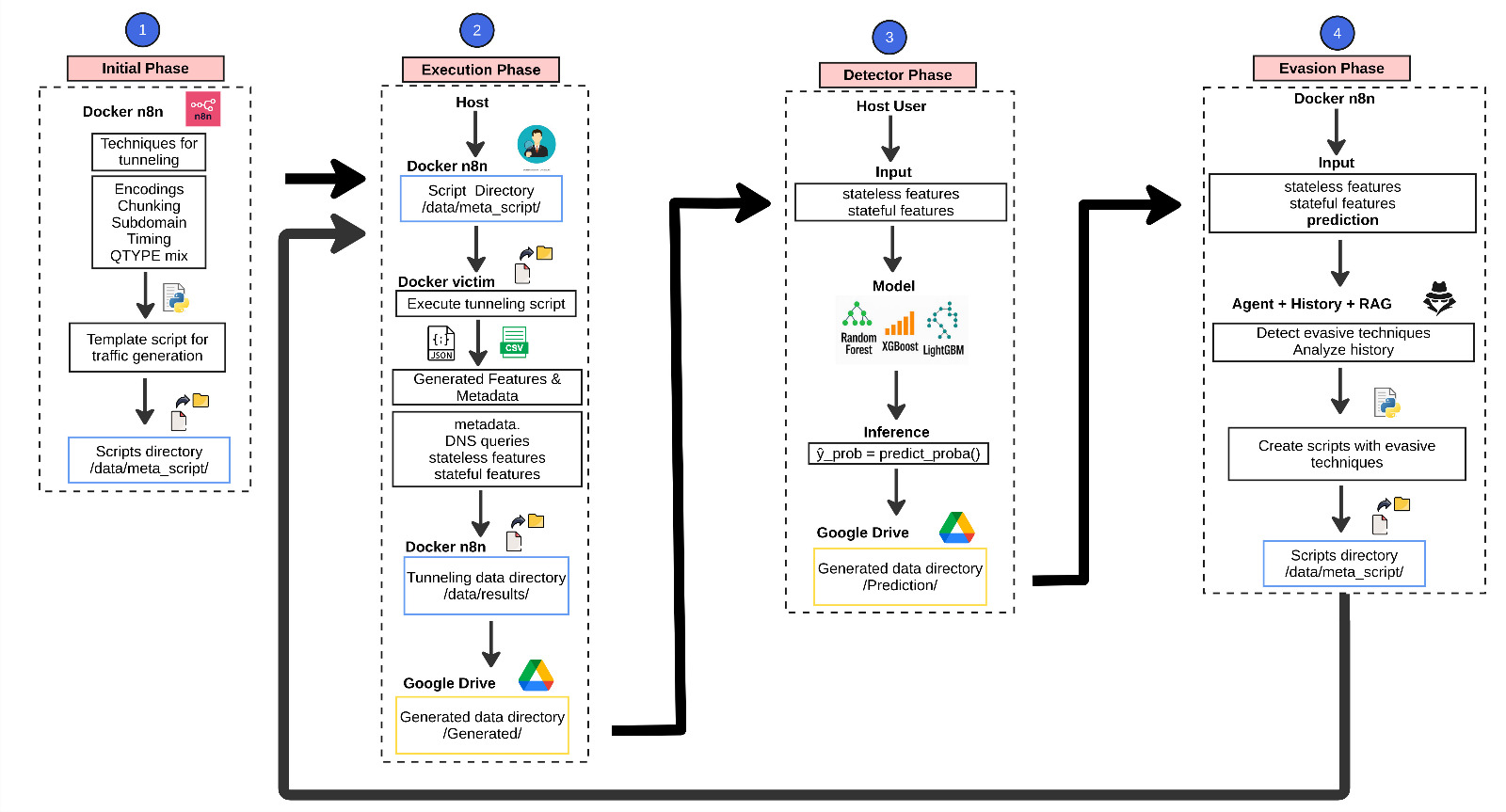
This research line focuses on developing modern defense techniques to detect and counter attacks that exploit the Domain Name System (DNS). The project addresses sophisticated threats including DNS tunneling, data exfiltration, and Domain Generation Algorithms (DGAs) used by advanced malware. Through the application of machine learning, adversarial methods, and language models with retrieval-augmented generation (RAG), the research aims to build adaptive detection systems capable of responding to evolving attack strategies. Key areas include the development of specialized DGA detectors designed for high precision, fast detection with low computational cost, and minimal false positive rates, validated across both known and novel DGA families. The research also establishes experimental environments that simulate adaptive attacker behavior, producing realistic evasive tunnels and datasets that expose weaknesses in existing detection systems. A distinctive aspect of this work is the automation of the entire testing and analysis pipeline using workflow platforms, enabling reproducible experiments, continuous attack-defense cycles, and scalable evaluation processes. Additionally, the project explores generative AI to simulate intelligent adversaries that learn from detector behavior and adapt their strategies, creating pressure that drives the development of more robust defense mechanisms. This work emphasizes solutions that combine high accuracy, fast decision-making, resistance to adaptive attackers, strong automation, and rigorous scientific validation for deployment in real-world environments.
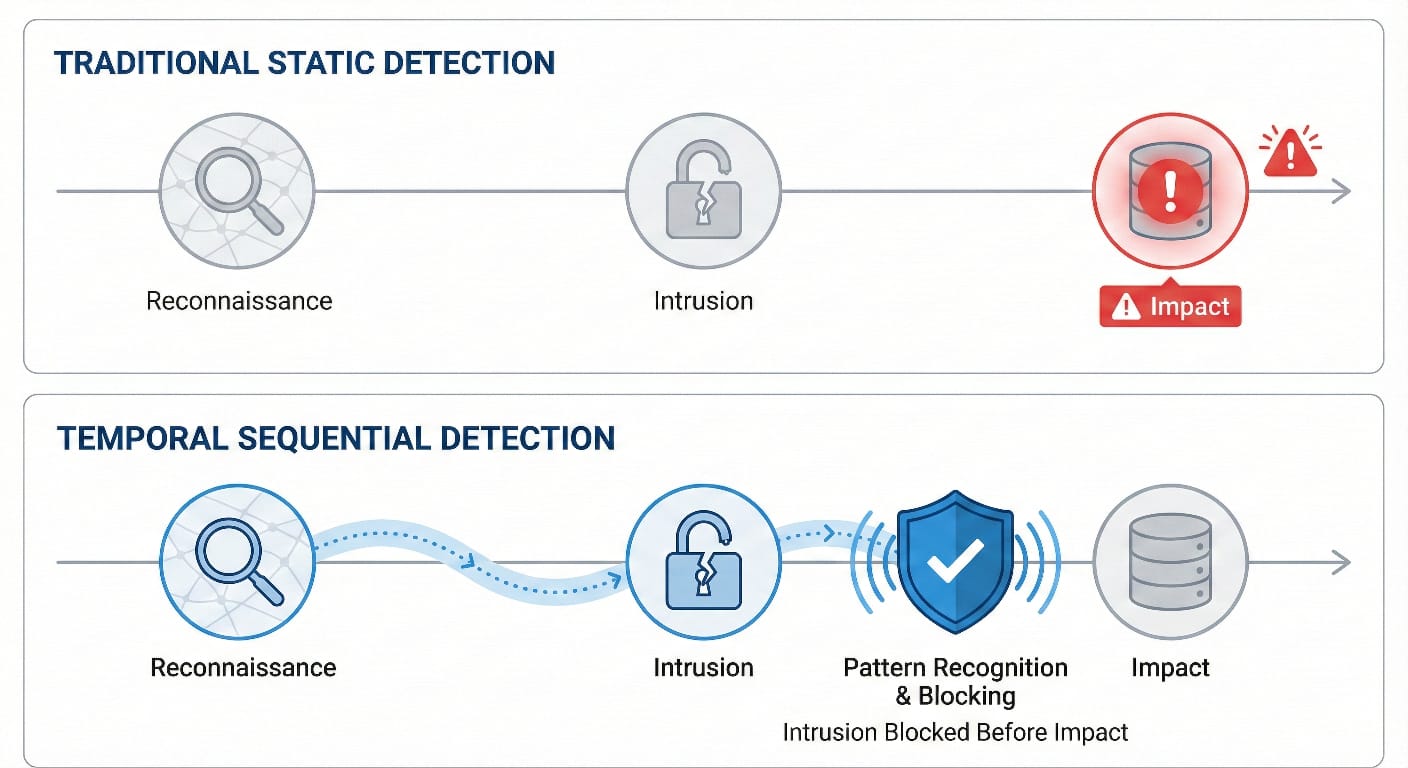
Traditional Network Intrusion Detection Systems (NIDS) often suffer from a critical limitation: they excel at detecting attacks only after significant damage has occurred, detecting late-stage tactics rather than early indicators of compromise. Most current techniques analyze network traffic as isolated static snapshots, failing to capture the sequential dependencies inherent in sophisticated cyber campaigns. This project addresses these shortcomings by developing time-aware detection frameworks that integrate temporal analysis into cybersecurity. By leveraging sequential Deep Learning models to analyze the chronological evolution of inter-flow behaviors and temporal windows, we aim to identify subtle adversarial patterns in early lifecycle stages. This approach enables proactive threat interdiction, shifting the defense paradigm from reactive forensic analysis to preventive security before the Impact phase.
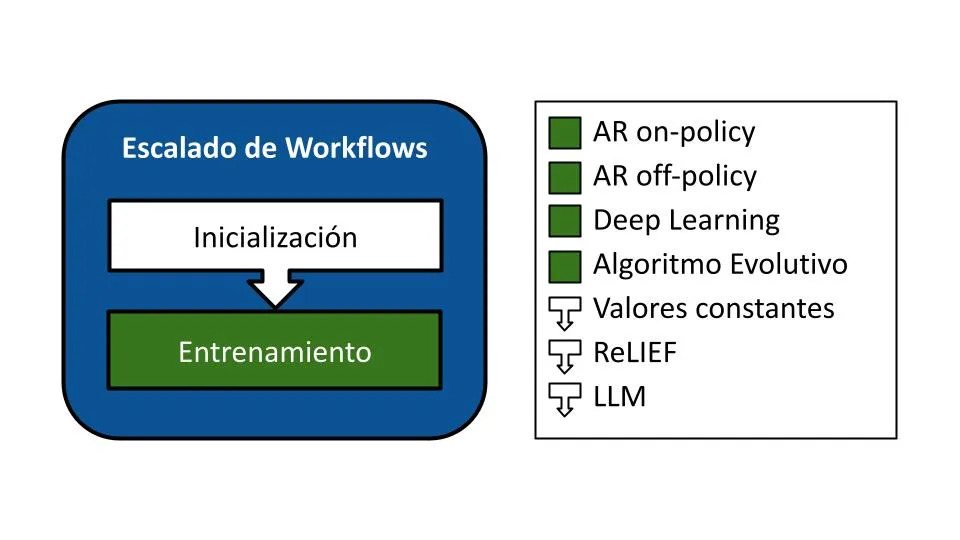
Scientific workflows are increasingly used to efficiently process large volumes of data in distributed systems. The scalability of computational resources in cloud environments is a critical factor for optimizing the performance and execution cost of these workflows. This project focuses on developing autoscaling strategies based on Reinforcement Learning to dynamically manage resources in complex scientific workflows.
The central objectives are designing a simulation environment that faithfully replicates distributed infrastructures; implementing Reinforcement Learning algorithms to learn optimal autoscaling policies; and optimizing metrics such as execution time, monetary cost, and service quality. The methodology is based on the neuroevolution approach, which combines neural networks with genetic algorithms to automatically evolve adaptive policies without relying on traditional gradient-based techniques.
The approach is validated using Montage and Epigenomics, scientific workflows with task and data dependencies that accurately represent real-world scenarios. These case studies allow evaluating the behavior of autoscaling policies under different conditions and workload patterns, demonstrating the capacity of Reinforcement Learning to adaptively balance the trade-off between performance and cost in dynamic cloud environments.
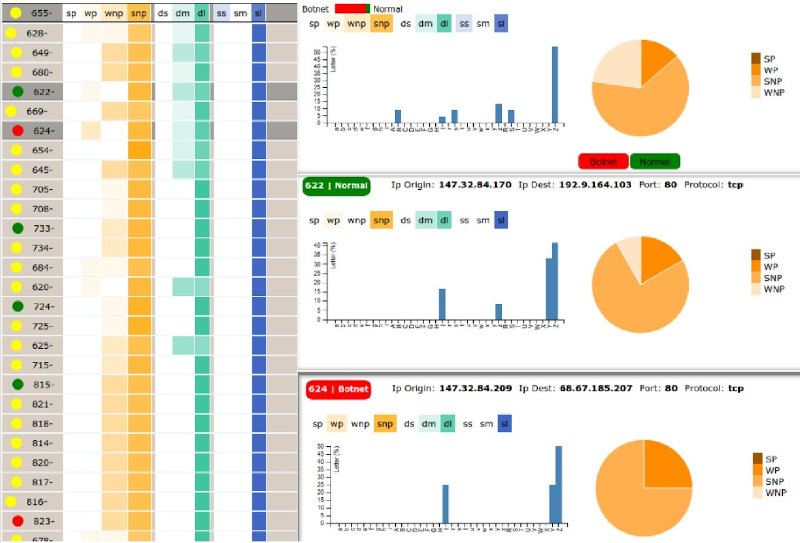
The recognition of malicious behavior in network traffic requires a big amount of resources, both human and computational. During the last few years, several approaches have been applied to try to alleviate the tasks of recognition and analysis. These approaches aim at making the task of netork security personnel easier, thus improving their ability to detect these behaviors and trying to increase the automation level of the process of malicious behaviors analysis and recognition. To this end, this project studies recommendation systems and their application to assist in the identification of threats to security in the network. In the labeling stage the goal is to assist in building a behavior model with a set of patterns compiled by experts using visual tools. Additionally, in the learning stage, supervised learning algorithms will be researched, to assist in the process of recommending labels for the traffic under analysis.

Head
PhD in Computer Science (UNICEN, Argentina). Free software activist.
Interests: Machine Learning applied to navigation systems, agriculture, livestock, network security, distributed systems, information networks.

Deputy head
PhD in Computer Science (UNICEN, Argentina).
Interests:
Metaheuristics, Reinforcement Learning, Deep Learning, Optimization, Autoscaling, Distributed Computing, Cloud Computing.

Researcher
PhD in Artificial Intelligence (Polytechnic University of Madrid, Spain).
Interests: Applied Artificial Intelligence, Planning and Scheduling, Logistics and Industrial Systems.

Researcher
PhD in Computer Science (UNICEN, Argentina). B.S. in Computer Science (University of La Habana, Cuba).
Interests: Machine Learning, Data Analysis, Visualization, Network Security, Sequence Analysis.

PhD Student
B.S. in Mathematics (National University of Cuyo. PhD student (Computer Science program, UNICEN, Argentina). CONICET Fellow 2021 -26.
Interests: Complex Networks, Data Analysis, Machine Learning, Deep Learning.

PhD Student
BSc in Physics (Universidad Nacional de Cuyo, Instituto Balseiro). MSc in Physics (Universidad Nacional de Cuyo, Instituto Balseiro). PhD student (Computer Science program, UNICEN, Argentina). CONICET Fellow 2022-2027.
Interests: Data Analysis, Machine Learning, Deep Learning, Scaling and Scheduling, Distributed Systems.

Undergraduate Student
Computer Science student (National University of Cuyo, Argentina).
Interests: Intelligent Agents, Cybersecurity, Machine Learning.

Undergraduate Student
Computer Science student (National University of Cuyo, Argentina).
Interests: Intelligent Agents, Cybersecurity, Machine Learning.

Undergraduate Student
Computer Science student (National University of Cuyo, Argentina).
Interests: Intelligent Agents, Cybersecurity, Machine Learning.

Undergraduate Student
Computer Science student (National University of Cuyo, Argentina).
Interests: Intelligent Agents, Cybersecurity, Machine Learning.
Address
Facultad de Ingenieria
Universidad Nacional de Cuyo
Centro Universitario. Parque Gral. San Martín
Mendoza. Argentina.
Phone
++54-261-4135000 ext. 2128
Email Address
labsin@ingenieria.uncuyo.edu.ar
You could also be interested in our code repository and publications.
Are you interested in developing research with us?
Do you need training or consulting?
Do you have projects requiring Artificial Intelligence?
Contact us!